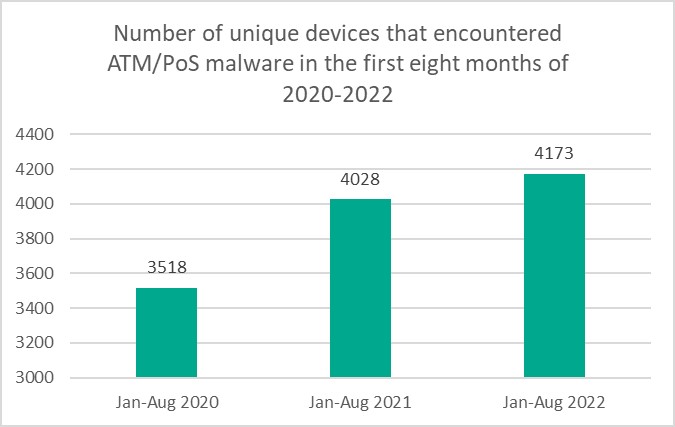
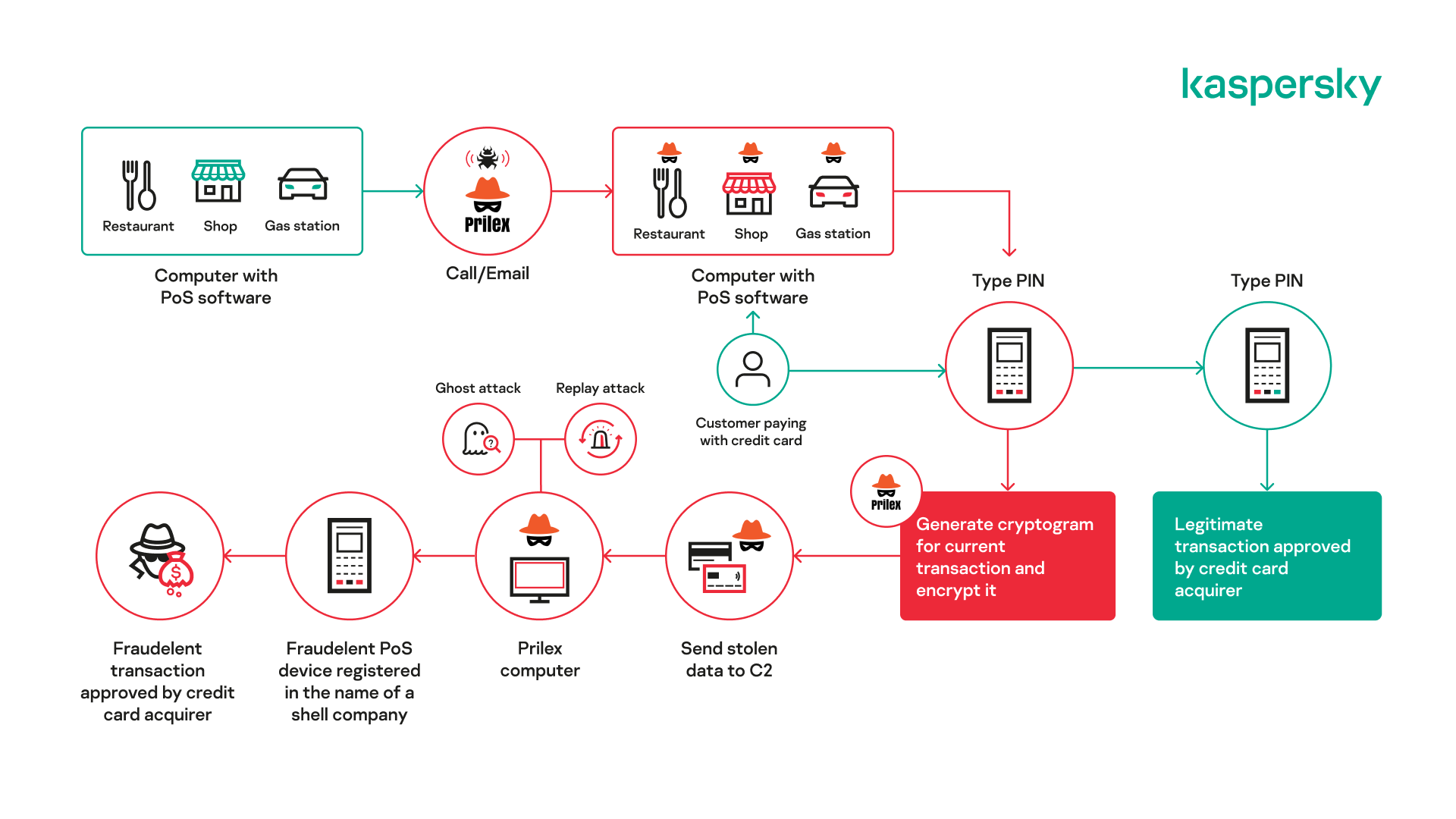
ATM/PoS malware “recovers” from covid-19, with the number of attacks continuing to grow in 2022 | Kaspersky

How PoS networks are protected from 51% attacks | by Cardanians.io (CRDNS pool) | Coinmonks | Medium

5 Facts You Might Have Missed About PoS Attacks of Recent Years - Wiadomości bezpieczeństwa - Trend Micro PL



















:max_bytes(150000):strip_icc()/Term-Definitions_Proof_Of_Stake_V1-2fe2af764d9c404e8c387224e4f69f60.jpg)


