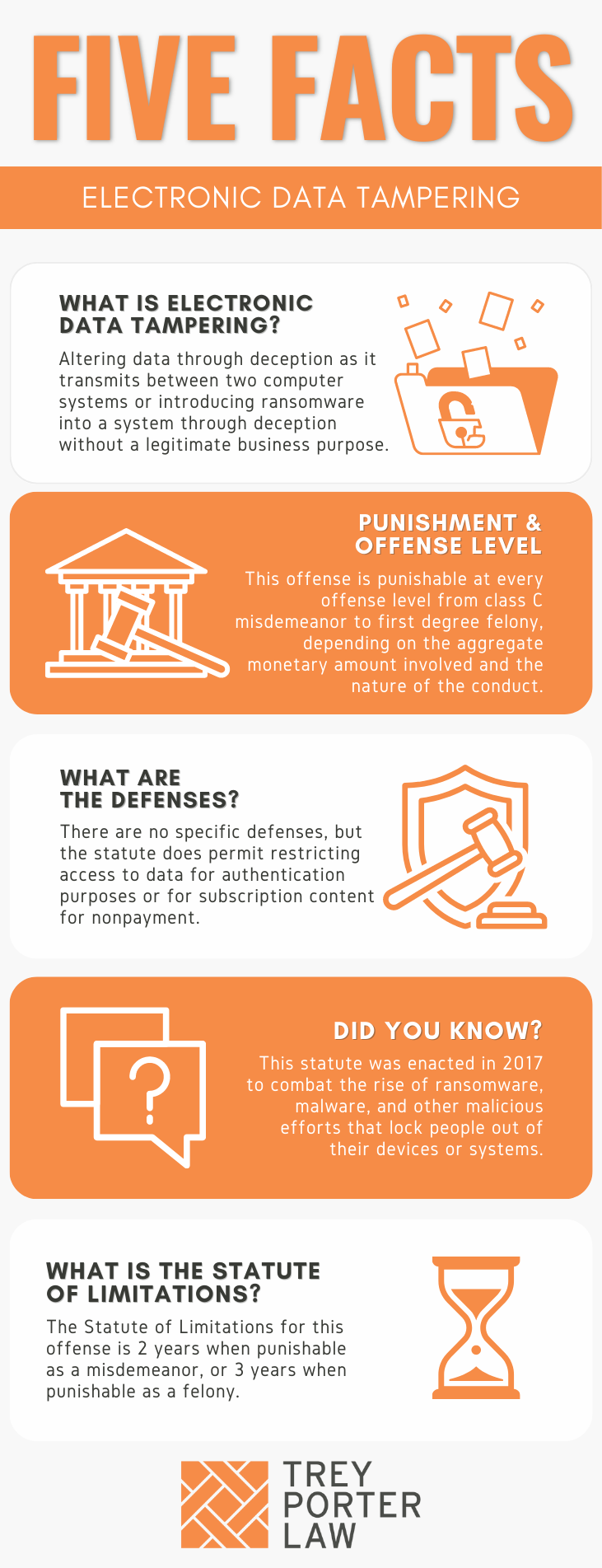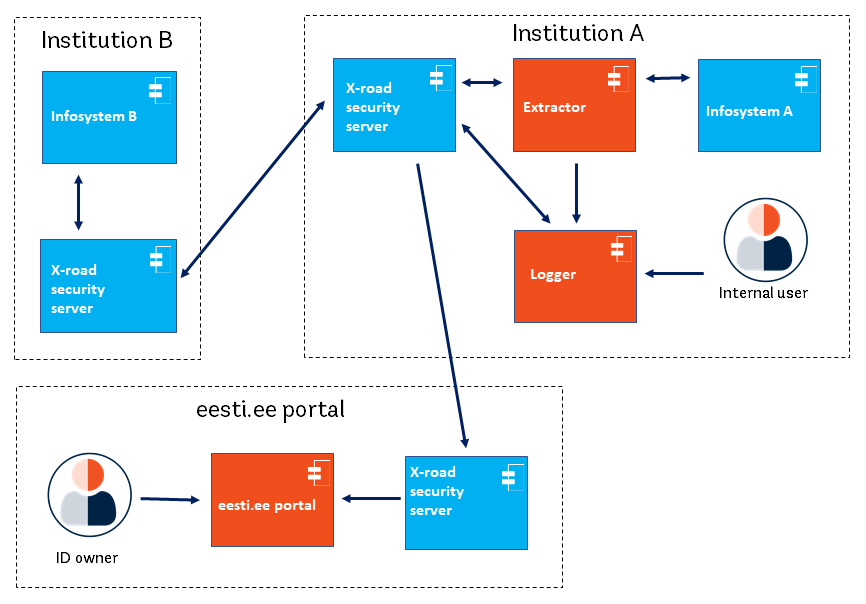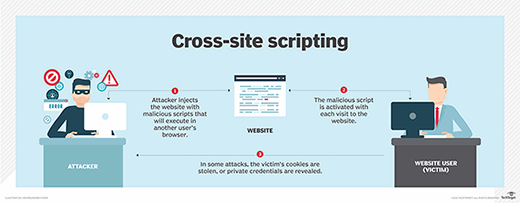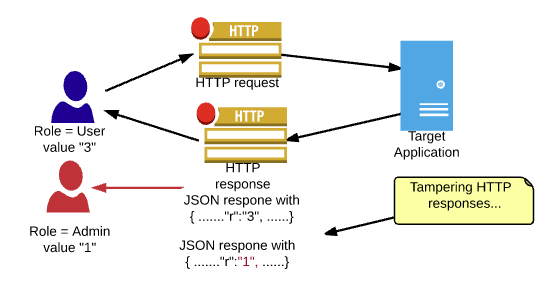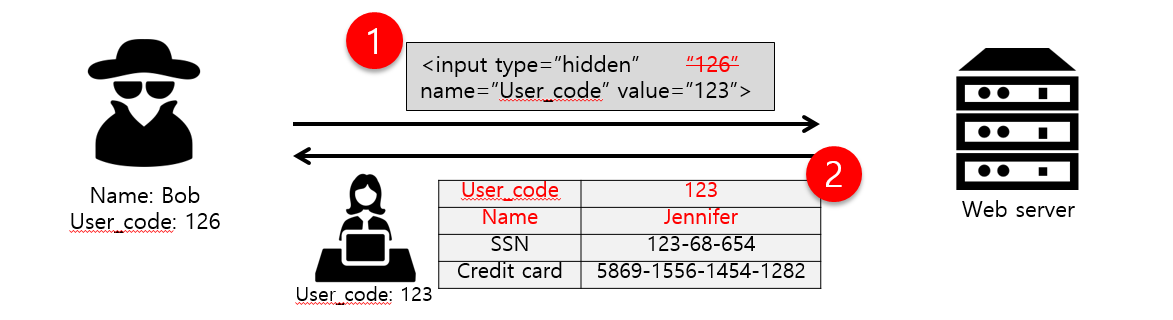
What is Parameter Tampering. Parameter Tampering: Special Characters | by MRunal | InfoSec Write-ups

Parameter tampering cyberattack and event-trigger detection in game-based interactive demand response - ScienceDirect

Database Tampering and Detection of Data Fraud by Using the Forensic Scrutiny Technique | Semantic Scholar
Two fingers are decorated as two person. They are discussing about data tampering Stock Photo - Alamy